M. El Hariri, T. A. Youssef, Abla Hariri, Student Members, IEEE and O. A. Mohammed, Fellow, IEEE
Energy Systems Research Laboratory, Florida International University, Miami, Florida, USA
The evolution rate of the power industry is increasing year after year. Over the past decade or two, this progress has been culminated by the emergence of the concept of Smart Grids, which is seen as a power system with real-time communication and control capabilities between energy providers on the one hand and energy consumers on the other. This modern power system model allows facilities to adopt new technologies and consumers to perceive new services. Utilizing communication technologies, the smart grid topology allows optimization of energy usage based on several factors including environmental, price preferences, and system technical issues [1]. The term Smart Grid may refer to large systems with large number of interacting energy production sources and energy consumption components. However, the same real-time communication and control capabilities can be applied to smaller scale systems such as Microgrids. The Department of Energy (DoE) defines a microgrid as “a group of interconnected loads and distributed energy resources within clearly defined electrical boundaries that act as a single controllable entity with respect to the grid” [2].
The concepts of smart grid and microgrids widened the thought horizons and altered the perspectives of other industry sectors. One significant example is the introduction of electric vehicles (EV) in the transportation industry. EVs have their energy stored in batteries and thus have limited operation time. Therefore, EV’s need to be recharged regularly. This fact introduces a whole new set of complexities to power system operations; one of which is related to the effect they have on load-demand profiles. It is a common practice to divide energy consumers into residential, commercial and industrial loads with load-demand profiles which can be forecasted with an acceptable accuracy. Conversely, energy consumed by EV is stochastic in nature and is hard to predict. Several factors are incorporated in this issue including individual driving preferences, manufacturers’ specifications, trips durations, etc. In fact, extensive ongoing research efforts have been placed on EVs, whether plug-in or wirelessly charged, in areas related to design optimization, charge control, efficiency boosting, large scale penetration of EVs into the smart grid, and many others [3][4][5][6].
In the Smart Grid era, EVs are gaining increased attention from various sectors. Given the increased demand for power, researches are looking at energy transaction algorithms between smart grids and electric vehicles which not only sell power to EVs, but also draw power from them when this power is available and needed. Here, design of a bidirectional power flow model for EVs to support Grid-to-Vehicle (G2V) and Vehicle-to-Grid (V2G) power flow is viable. Looking at an EV as an energy consumer and an energy producer, simultaneously, with grid connection capabilities, leads us to define EVs as mobile microgrids or microgrids on wheels. Therefore, integration of EVs with the electric grid must be handled with extreme care and studied from various perspectives. While bringing a lot of benefits to its owners in terms of cost savings, especially with the work being done on energy management systems, EV charging, when looked at as a cyber-physical system, puts car owners at risk of several attacks. As detailed later in this paper, these attacks range from fabricating price information to completely shutting off a charging session. Like any other modern process, data exchange is a prerequisite for implementing EV charging processes. A major issue to look at, therefore, is the cyber security of EV-Grid interactions.
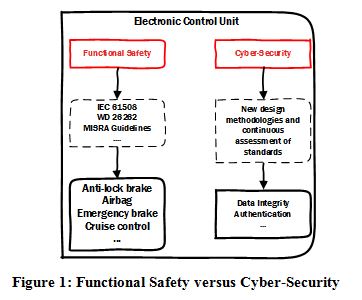
Today, each EV comes with onboard Electronic Control Units (ECU) which hold the vehicle’s information and manages communication with charging stations. In fact, there are efforts to standardize EV-Grid communication such as ISO/IEC 15118 and SAE J9231. However, robustness of these standards lags behind in issues related to identity authentication and data integrity, confidentiality, and privacy [7]. Since the electric vehicle technologies are in the early development stage, it provides a key advantage to researchers to incorporate cyber-security into their design methodologies from the beginning of the development process. Here, it is important to realize the difference between the “functional safety” and “cyber security” as shown in Figure 1. ECUs in the automotive industry are software intensive units and are used to control a wide range of safety-critical issues such as emergency brake assist, cruise control, and anti-lock braking systems to name a few. Functional safety measures, such as IEC 61508, WD 26262, and MISRA Guidelines, have been well addressed in the literature and are applied in automotive industry to ensure continuous safe operation of the vehicle. From a cyber-security perspective, this article exploits vulnerabilities in the EV charging process and guides researchers into the direction of designing robust and highly secure EV ecosystem which will safely integrate with the power grid.
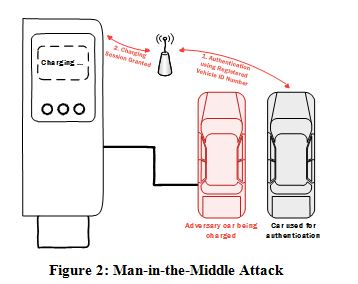
It is well known that generation-load balancing in power systems is not an easy task to perform. The introduction of the EVs into this equation complicates things further. Therefore, a lot of feedback control is being developed and implemented on charging stations to maintain a stable power system. That is, when connected to a charging station, the EV’s charging profile must always be monitored and the EV itself must properly respond to command signals coming from the charging station. It is imperative that such commands come from an authentic source (the charging station) and reach the required host (authenticated EV) unaltered. In a typical charging scenario, an EV arrives at a charging station and requests a charging session. As stated by IEC 15118, each EV must have a secret key stored in one of it ECUs. If the control station verifies the car’s key through wireless communication, the charging process can be easily compromised by a Man-in-the-Middle (MIM) attack [8]. It was shown that a registered car with a valid key performs the authentication process and the charging cable is connected to a stolen car as outlined in Fig. 1. Not only does MIM attacks allow charging of unregistered cars, but also the firmware on the stolen car’s ECU can be modified as not to respond to commands from the charging station. It is to be noted that modifying a vehicle’s ECU is not an easy task; however, it is not impossible. In fact, the authors in [9] were able to reprogram the firmware on a 2010 Ford Escape and a 2010 Toyota Prius ECU. Such an attack can interfere in or block vehicle-to-grid services.
Today, EV charging stations can be found in public places such as airports, mall parking’s, and roadsides. They are thus exposed to public and vulnerable networks. Although security practices are being standardized, it is imperative to continuously evaluate these standards to ensure high security levels. In fact, [10] disclosed two weaknesses in the NISTIR 7628 security framework in context of EV infrastructure: one related to the device authentication and the other to location privacy. EVs charging process is thus prone to other types of attacks including eavesdropping, denial of service, and data spoofing. It is important to understand how these attacks are implemented in order to study their consequences on the EV charging ecosystem and to take appropriate defense mechanisms.
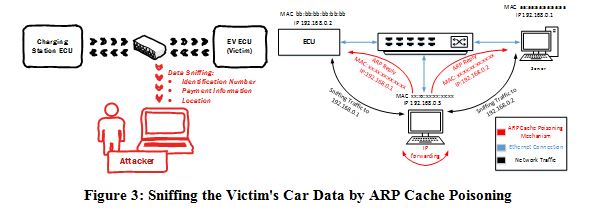
1) Eavesdropping: In this type of attacks it is assumed that the attacker has access to the Local Area Network (LAN) of the charging station. After breaching the network, the attacker can sniff and store all the data being communicated between the charging station and the electric vehicle as shown in Fig. 2. For example, the LAN can be penetrated by Address Resolution Protocol Cache Poisoning,
IEC 15118 states that before initiating a charging session, an Identification and Authentication process must be performed in order to check the EV’s identity. In this process, the car’s Identification Number, which is a unique number stored in the vehicle’s ECU, is exchanged with the charging station over the LAN. An attacker eavesdropping on the network can get hold of the ID of the EV. Although IEC 15118 established the requirement of using Transport Layer Security (TLS) for communicating data, TLS itself can be compromised [11][12]. With the knowledge of an EV’s ID, an attacker can download this ID into an ECU of a stolen or an unregistered car and initiate detestable charging sessions. Not only the EV’s ID is compromised, but also is the payment information of the attacked vehicle’s owner. Charging of unregistered vehicles with fake ID’s could lead to financial losses to both the car owner and to the power company.
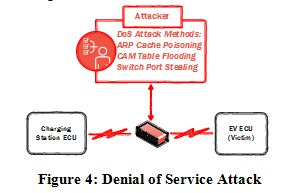
2) Denial of Service: Denial of Service (DoS) attacks put the grid and the EV at risk. As shown in Fig. 3, DoS is when an attacker blocks an entity from accessing a given service. Technically, DoS can be achieved by flooding the network. That is, the attacker attempts to obstruct the communication channels and expend the computational resources of the communicating nodes by delaying message delivery past a critical flooding rate. Here again, blocking a control signal coming from the charging station from reaching the ECU on the EV will prevent the vehicle from responding to serious grid commands such as load shedding. An attacker might as well block the whole charging process leading to inconvenience to the car’s owner.
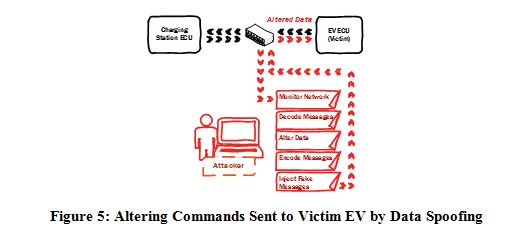
3) Data Spoofing: After blocking the communication link between the charging station and an EV by a successful DoS attack, an attacker might inject false or malicious data both to the charging station and to the EV as shown in Fig. 4. With accurate knowledge of data and message types, the probability of a successful data spoofing attack is relatively high especially that IEC 15118 relies on the Public Key Infrastructure (PKI) approach. Although PKI helps authenticate identities on a network by a chain of trust of digital certificates, this infrastructure is as strong as the weakest device on the network. Interfering with communication messages in the context of EV charging opens the road to many fraudulent and hazardous acts. Such acts may cause network congestions, delay of successful delivery of legitimate messages, and disruption of services [13]. The authors in [13] also explained that modifying pricing signals sent to EVs to be very low but could result in a large number of vehicles requesting charging sessions simultaneously leading to unstable grid operations or at a larger scale could possibly lead blackout.
From a broader viewpoint, the attacks on a vehicle are not only limited to the charging process. The onboard computers, on current vehicles, can be categorized as computers for
controlling the car’s Entertainment Systems and computers for controlling and monitoring the car operation itself such as keyless ignition, dynamic breaking, and anti-lock brake control among others. Rigid security of communication channels between these onboard computers was not an issue when they first came into market as they were considered to operate within the car’s isolated network. However, entertainment systems of new vehicles come with Universal Serial Bus (USB) ports for connecting electronic devices and also internet connectivity over mobile networks (GPRS, 3G, and 4G). The vehicle’s network is no longer isolated. Using the entertainment system’s network as an entry point, an attacker can benefit from open ports to hack into other ECU’s controlling critical operations such as braking, steering, or even shutting the vehicle off. In fact, researchers Miller and Valasek published their work “Remote Exploitation of an Unaltered Passenger Vehicle” in August 2015 where they were able to hack into a Chrysler Jeep remotely and control any service in the car which is controllable over the in-car network. The researchers used the U-Connect entertainment system in the Jeep as an entry point to the car network. This astounding work got a lot of attention from the media as it was applied on a real commercial vehicle which people are already driving. Yet again, it is highly recommended to look into securing all communication links inside a vehicle starting from the planning and design stages.
The likelihood of electric vehicles charging process to be besieged by various attacks is now evident. Each type of attack has its own objective and possess critical consequences both to the grid and to the EV itself. These consequences, being grid instability, energy theft, false identification, jeopardizing EV owner’s personal security and others are not to be belittled. IEC 15118 did publish security standards for communications regarding charging electric vehicles but its resiliency against the previously mentioned attacks is still debatable. A lot of thought on designing EV charging stations is being made and consideration regarding the security of these systems ought to be considered and utilized at early design stages.
Recently, industry and academic research are gaining insight at the importance of securing EV charging process and work is starting to be done to defend against some type of attacks. In 2014, the authors of [8] proposed a cyber-physical EV authentication mechanism to eliminate the substitution attack, which is a type of MIM attack. Following successful vehicle authentication by the charging station occurring over a wireless communication medium, another physical challenge is sent over the control pin of the charging cable to make sure that the claimed authenticated car is actually the one being charged and not an adversary one. This approach is tailored and well suited for plug-in electric vehicles and does not account for the next generation wirelessly charged electric vehicles. In the latter, there is no charging cable and thus the proposed defense mechanism is not adequate.
In another recent approach, work in [14] looked at a comprehensive demand side management system with stringent security mechanisms for safe integration of electric vehicles with the smart grid. First, the authors identified the importance of power grids having full access control of the charging process in order to ensure stable and reliable grid operation. Then they started designing their system from a physical and cyber perspective simultaneously. Key to their work is the digital identity assurance of electric vehicles for safe integration with the power grid. One might argue that this system uses legacy cryptographic techniques for digital devices identification and data encryption; however, a big advantage of this work is the thought process followed by the authors where security was tailored in starting from the planning and system design phases.
The smart grid as proposed in [15] is divided into five broad components namely “Smart Power Grid”, “Smart Consumer”, “Smart Electricity Service”, “Smart Renewable”, and “Smart Transportation”. These are all still envisioned futuristic concepts which are undergoing extensive research and investigation both nationally and internationally. Contrary to the legacy power systems communications networks which were designed to operate in close environments, it is about time that communication security is placed at the top of the table in designing the future smart power grid in all its components including EV ecosystem. This paper exploited the shortcomings of current EV-Grid integration systems and investigated the drawbacks of security breaches on the power grid, EV itself, and the safety of the vehicles’ owners in hope of advocating a new thought philosophy that gives the same importance for system operation and system security. Electric Vehicles are indeed microgrids on wheels, but for them to be widely integrated with the smart grid, their security has to be placed in the front seat and left behind.
References
[1] Vahid Salehi, Ahmed Mohamed, Ali Mazloomzadeh, Osama A. Mohammed, “Laboratory-Based Smart Power System, Part I: Design and System Development,” IEEE TRANSACTIONS ON SMART GRID, vol. 3, no. 3, September 2012.
[2] U.S. DOE MEG: https://building-microgrid.lbl.gov/microgrid-definitions
[3] [S. Deilami, A. S. Masoum, P. S. Moses and M. A. S. Masoum, “Real-Time Coordination of Plug-In Electric Vehicle Charging in Smart Grids to Minimize Power Losses and Improve Voltage Profile,” in IEEE Transactions on Smart Grid, vol. 2, no. 3, pp. 456-467, Sept. 2011. doi: 10.1109/TSG.2011.2159816
[4] Y. Cao et al., “An Optimized EV Charging Model Considering TOU Price and SOC Curve,” in IEEE Transactions on Smart Grid, vol. 3, no. 1, pp. 388-393, March 2012. doi: 10.1109/TSG.2011.2159630
[5] L. Pieltain Fernandez, T. Gomez San Roman, R. Cossent, C. Mateo Domingo and P. Frias, “Assessment of the Impact of Plug-in Electric Vehicles on Distribution Networks,” in IEEE Transactions on Power Systems, vol. 26, no. 1, pp. 206-213, Feb. 2011. doi: 10.1109/TPWRS.2010.2049133
[6] O. Sundstrom and C. Binding, “Flexible Charging Optimization for Electric Vehicles Considering Distribution Grid Constraints,” in IEEE Transactions on Smart Grid, vol. 3, no. 1, pp. 26-37, March 2012. doi: 10.1109/TSG.2011.2168431
[7] S. Lee, Y. Park, H. Lim and T. Shon, “Study on Analysis of Security Vulnerabilities and Countermeasures in ISO/IEC 15118 Based Electric Vehicle Charging Technology,” IT Convergence and Security (ICITCS), 2014 International Conference on, Beijing, 2014, pp. 1-4. doi: 10.1109/ICITCS.2014.7021815
[8] A. C. F. Chan and J. Zhou, “Cyber–Physical Device Authentication for the Smart Grid Electric Vehicle Ecosystem,” in IEEE Journal on Selected Areas in Communications, vol. 32, no. 7, pp. 1509-1517, July 2014. doi: 10.1109/JSAC.2014.2332121
[9] Charlie Miller and Chris Valasek, “Adventures in Automotive Networks and Control Units”,http://www.ioactive.com/pdfs/IOActive_Adventures_in_Automotive_Networks_and_Control_Units.pdf
[10] A. C. F. Chan and J. Zhou, “On smart grid cybersecurity standardization: Issues of designing with NISTIR 7628,” in IEEE Communications Magazine, vol. 51, no. 1, pp. 58-65, January 2013. doi: 10.1109/MCOM.2013.6400439
[11] N. J. Al Fardan and K. G. Paterson, “Lucky Thirteen: Breaking the TLS and DTLS Record Protocols,” Security and Privacy (SP), 2013 IEEE Symposium on, Berkeley, CA, 2013, pp. 526-540. doi: 10.1109/SP.2013.42
[12] K. Bhargavan, A. D. Lavaud, C. Fournet, A. Pironti and P. Y. Strub, “Triple Handshakes and Cookie Cutters: Breaking and Fixing Authentication over TLS,” 2014 IEEE Symposium on Security and Privacy, San Jose, CA, 2014, pp. 98-113. doi: 10.1109/SP.2014.14
[13] M. A. Mustafa, N. Zhang, G. Kalogridis and Z. Fan, “Smart electric vehicle charging: Security analysis,” Innovative Smart Grid Technologies (ISGT), 2013 IEEE PES, Washington, DC, 2013, pp. 1-6. doi: 10.1109/ISGT.2013.6497830
[14] A. C. F. Chan and J. Zhou, “A Secure, Intelligent Electric Vehicle Ecosystem for Safe Integration With the Smart Grid,” in IEEE Transactions on Intelligent Transportation Systems, vol. 16, no. 6, pp. 3367-3376, Dec. 2015. doi: 10.1109/TITS.2015.2449307
[15] S. Lee, Y. Park, H. Lim and T. Shon, “Study on Analysis of Security Vulnerabilities and Countermeasures in ISO/IEC 15118 Based Electric Vehicle Charging Technology,” IT Convergence and Security (ICITCS), 2014 International Conference on, Beijing, 2014, pp. 1-4. doi: 10.1109/ICITCS.2014.7021815
|
|
Mohamad A. El Hariri is currently a Ph.D. student and Research Assistant at the Energy Systems Research Laboratory at Florida International University. He received his B.Ss. and M.Sc. degree in Mechatronics Engineering with distinction from Rafik Hariri University, Mechref, Lebanon, in 2012 and 2014 respectively. Between 2014 and 2015, Mohamad was a technical projects engineer at National Oilwell Varco, Dubai. Mohamad’s research includes cyber security for cyber-physical systems, computational electromagnetics, and artificial intelligence techniques in power system applications. |
|
|
Tarek A. Youssef was born in Cairo, Egypt. He received the B.S. and M.S. Degrees in Electrical Engineering from Helwan University, Cairo, Egypt. Tarek has more than 10 years experience in communication and security filed. He worked as a researcher in the Université Libre de Bruxelles, Belgium. In 2012 Tarek moved to Energy Systems Research Laboratory, Florida International University. He is currently a Ph.D. candidate. His Ph.D. Topic is Co-Design of Security Aware Power System Distribution Architecture as Cyber Physical System. His research interests include cyber physical systems, communication, Wide area measurement, smart grid security, and real time monitoring of power system. Furthermore, he also has interest in artificial intelligence and signal processing applications in the power and energy systems area. |
|
|
Abla Hariri received her B.Sc. and M.Sc. degrees in Electrical Engineering from Rafik Hariri University, Mechref, Lebanon, in 2012 and 2014 respectively. She is currently a Research Assistant and working towards her Ph.D. degree at the Energy Systems Research Laboratory in the Electrical and Computer Engineering Department, College of Engineering and Computing, Florida International University. Her research interests include the Wireless Charging of Electric Vehicles, on a system level, and Large Scale Penetration of Electric Vehicles in the Power Grid. |
|
|
Osama A. Mohammed (S’79–SM’84–F’94) is a Professor of Electrical Engineering and is the Director of the Energy Systems Research Laboratory at Florida International University, Miami, Florida. He received his Master and Doctoral degrees in Electrical Engineering from Virginia Tech in 1981 and 1983, respectively. He has performed research on various topics in power and energy systems and their cyber physical and communication infrastructures. Additionally, he has interest in computational techniques and design optimization in electric drive systems and other low frequency environments. He performed multiple research projects for several Federal agencies since 1990’s dealing with; power system analysis, physics based modeling, EMI and EM signatures, sensorless control, high frequency switching. He also performed funded research in ship power systems as well as energy cyber physical systems and transportation electrification. Professor Mohammed has currently active research programs in a number of these areas funded by DoD, the US Department of Energy and several industries. Professor Mohammed leads the currently funded DoE center for secure energy system infrastructure at FIU. Professor Mohammed is a world renowned leader in electrical energy systems, computations and intelligent systems. He has published more than 450 articles in refereed journals and other IEEE refereed International conference records. He also authored a book and several book chapters. Professor Mohammed is an elected Fellow of IEEE and is an elected Fellow of the Applied Computational Electromagnetic Society. Professor Mohammed is the recipient of the prestigious IEEE Power and Energy Society Cyril Veinott electromechanical energy conversion award and the 2012 outstanding research award from Florida International University. |
Read the article on IEEE Transportation Electrification Newsletter.
http://tec.ieee.org/newsletter/june-2016/microgids-on-wheels-not-to-leave-security-behind